|
|


- Instant Messaging & Peer-to-Peer
-
Peer to peer networking presents a serious threat in all its forms. These include
all types of Instant Messaging, file sharing and Internet telephony. Most users
are unaware of the risks posed by these technologies.
- Take file sharing for example:
Even if the apparent use seems innocuous, such as sharing music files or looking for extraterrestrial life, the user is granting unauthorized access to their computer and its resources to one or more unknown entities.
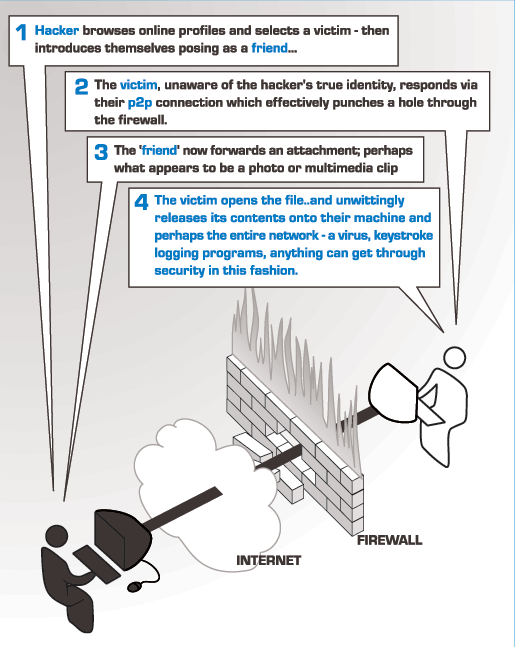
- Instant Messaging creates a hole,
or tunnel through the network's firewall, and uses it to transport text to another computer somewhere, and to receive text from unknown sources. At the time of this writing, most IM communication is unencrypted, although there seems to be a trend toward encryption. Should an IM application have security vulnerabilities, it would be possible for a remote hacker to gain access to the computer, or send an infected file.
- Internet telephony creates interest because of the obvious cost savings.
For this reason it is also viewed as a Good Thing, and avoids scrutiny. However, it uses up large amounts of bandwidth. Worse, it uses bandwidth not only for the user's own voice, but may effectively hijack their computer and use it as a telephone router for other calls. This abuse of bandwidth taxes network resources and costs everyone. Further, many network administrators do not like the idea of encrypted data running over their network with no idea of the source, destination, or contents.
- Loss of Productivity.
Chatting to friends or downloading software, music of videos can lead to
lost productivity and legal liability.
|
|
|

|



 Features
Features